Directory Structure
It is important to become familiar with the directory structure and operating system of any computer system. You need to save files with some organization method or directory structure. This is accomplished with the operating system. On a distributed c omputing system, such as a SUN, the operating system is UNIX. Using the operating system, you make directories and subdirectories that are used for storing files. Also you copy files and move them between different directories.
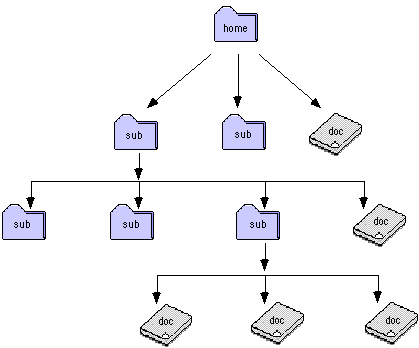
Your home directory is the one you start with once you have logged in. This directory, as with all directories, can contain files or more directories. A directory contained within another directory is called a subdirectory. A schematic of a directory structure is shown in Figure 1

Note:The H:\ storage on the CEE PC's is the same as your UNIX home directory. All files are common to both systems and are accessible from either the SUN's or the PC's. You may want to regularly backup your important files on the A:\ drives on th e PC's.
| cd | chmod | clear | cp | kill | logout |
| lpq | lprm | ls | man | mkdir | more |
| mv | passwd | ph | ps | pwd | rm |
| rmdir | sendfile | who | top |
| Introduction to Text Editors | Introduction to Operating Shells |
| .cshrc | .pinerc | .addressbook |
Change your password. User will be prompted for old and new password . The new password will be confirmed to minimize typographic errors.
logout (man pages for logout )
Logs you off the computer system. Always logout when you are finished.
man [command] (man pages for man )
Provides on-line manual for most UNIX commands. Good way of getting detailed information on any UNIX command. Example: man mv will provide a detailed listing of how the mv command works.
ls {-a} (man pages for ls)
List the files and sub-directories in a directory
Optional switches can be added after the ls command as follows
-a List all entries, including those that begin with a dot (.), which are normally not listed.
-A List all entries, including those that begin with a dot (.), with the exception of the working directory (.) and the parent directory (..).
-s Give size in blocks, including indirect blocks, for each entry.
-t Sort by time stamp (latest first) instead of by name. The default is the last modification time. (See -u and -c.)
-l List in long format, giving mode, ACL indication, number of links, owner, group, size in bytes, and time of last modification for each file (see above). If the file is a special file, the size field instead contains the major and minor device numbers. If the time of last modification is greater than six months ago, it is shown in the format `month date year'; files modified within six months show `month date time.' If the file is a symbolic link, the filename is printed followed by "->" and the path n ame of the referenced file.
skipDetailed Information on the ls switches
Using the -l switch, a long list is produced that shows the privilages on files and directories. An example of the -l list is given below:
rwxrwxrwx+ 1 smith dev 10876 May 16 9:42 part2
Reading from right to left, you see that the current directory holds one file, named part2. Next, the last time thatfile's contents were modified was 9:42 A.M. on May 16. The file contains 10,876 characters, or bytes. The owner of thefile, or the user, belongs to the group dev (perhaps indicating ``development''), and his or her login name is smith.The number, in this case 1, indicates the number of links to file part2; see cp(1). The plus sign indicates that thereis an ACL associated with the file. Finally, the dash and letters tell you that user, group, and others have permis-sions to read, write, and execute part2.
The execute (x) symbol here occupies the third position of the three-character sequence. A - in the third positionwould have indicated a denial of execution permissions.
The permissions are indicated as follows:
r the file is readable w the file is writable x the file is executable - the indicated permission is not granted
An example of a file's permissions is:
-rwxr--r--
This describes a file that is readable, writable, and executable by the user and readable by the group and others.
Another example of a file's permissions is: -rw-rw---
This describes a file that is readable and writable only by the user and the group
clear (man pages for clear)
Clears the screen of unwanted text and homes the cursor.
mkdir [directory] (man pages for mkdir )
Creates a new directory called directory .
cd {directory or path} (man pages for cd )
Change the directory to a specific directory described by the name directory or path:
cd with no specified directory takes you to your home directory.
cd_.. takes you back one directory
Copies a file
cp_ file1.f_ file2.f - copies file1.f to file2.f
mv [path1] [path2] (man pages for mv )
Moves or renames a file. The actual action of the mv command depends on the path specified.
mv_ file1.f_ file2.f - renames file1.f to file2.f
mv_ directory1_ directory2 - renames directory1 to directory2
mv_ file1.f_../ subdirectory1 - moves file1.f back one directory and puts it in the sub-directory called subdirectory1. In this
instance, the two dots indicate "back one directory" and the slash tells UNIX that subdirectory1 is a sub-director y, not a new file name.
rm [file1.f] (man pages for rm )
Removes a file named file1.f
You will be prompted to make sure you want to delete a file
rmdir [directory] (man pages for rmdir )
Removes a directory or sub-directory named directory
Directory must me empty to be removed
Displays the path to the current directory
more [filename] (man pages for more )
Displays the contents of a text file. This command is useful for viewing data files or some of the special files detailed later in this document. If the file specified is in fact a directory, the more command will inform you so. If the file specifi ed i s not a text file, the more command will attempt to list it but unintelligible characters will be displayed.
sendfile [file1.f] to [userid]
Used to send a file from one user to another. The above example sends the file file1.f to the user identified by userid. To receive a file, simply type sendfile with nothing else specified. A menu will be presented where you can read files that hav e been set. Sendfile puts the file in your current active directory. For example, if you execute a cd ~/public_html command before using sendfile, it will receive the files in your public_html directory.
ph [name]
Used to get the e-mail address of a person at MTU. Enter the person's last name. Example: ph sutter
chmod (man pages for chmod )
Used to change the privilages on a file or directory.
For more information on privilages see the ls command listing in this handout or use the man ls command at the UNIX prompt to get detailed information. Also, use the command man chmod to learn more about thechmod command.
Displays all active central processor jobs. Each job will be assigned a number. Jobs related to your work will be identified with your userid.
Lists only central processor jobs you currently have running. If the job is a printer job use the lpq command to view the printer queue.
Displays who else is running on your computer
kill [job number] (man pages for kill )
Terminates a central processor job. If the job is a printer job and is queued, kill will not terminate the printout
Display the printer queue to see if your document printed
lprm [job number] (man pages for lprm )
Kill a printer job. Obtain the print job number with the lpq command.
Programs to read your e-mail that can be exercised at the prompt
Text Editors
There are two different text editors available on the SUN systems. These programs can be used to generate or edit text files. One application is for generating source code for a FORTRAN compiler. The two editors are Pico and Vi. These text editors are also very useful for editing the Special Files listed later in this document.
Shells
The operation of UNIX can be tailored through the choice and modification of the UNIX shell. The shell defines things such as how the arrow keys manipulate the cursor, what special commands or aliases are defined, and the physical appearance of the G UI. Examples of shells are csh and tsh. In the Civil Computer labs, the default shell is csh. You may want to explore other shells and see if their operation is more suited to the way you work. There are files to customize your chosen shell. Typicall y, these files begin with a period (.) See the information on the ls command presented earlier in this document for listing these files These files can be edited with either the Pico or Vi. The function of some of these are described below. Consult a UNIX manual or a consultant to learn about the others.
This file can be used to establish alias' for UNIX commands. For commands that are used often, assign an alias so the command can be executed by typing one or two letters. The .cshrc file, like all text files, can be viewed with the more com mand. An example .cshrc file is shown below:
Example of a .cshrc file
source /usr/dept/lib/stdcshrc
alias p 'pine'
alias ll 'logout'
alias c 'clear'
alias k 'fixkbd'
alias h 'cd public_html'
alias i 'pico index.html'
The syntax is:
alias xx ' command'
where xx are the key or keys used to execute the command and command is the command stream to be executed. The single quotes around the command are optional.
If you change your .cshrc file, you need to institute the changes. You can accomplish this task two ways. The best way is to return to the UNIX command line and type the following command
source .cshrc
Alternatively, you can logout and then log back in to institute the changes.
This file contains information that can be used to customize Pine. The file is to large to include here but an excerpt is shown below to illustrate its structure.
personal-name=
user-domain specifies the domain part of your return address on outgoing e-mail and is also used as the default domain for email composed to a local user. If not set, UNIX Pine will obtain the domain from the system.
user-domain=
To customize Pine, enter information after the equals sign. For example, if you enter your name after personal-name=, then every e-mail message you send will have your e-mail address and your real name on the From line. Pine can get your real name other ways but this allows you to customize this information. For example, the real name that Pine has access to for you may be a formal full name such as Richard Smith. However, you may want to go by Rich Smith. Entering Rich Smith on this line overrides t he other information Pine has access to. Read the complete .pinerc file and set the parameters that you want to set. As a side, it is recommended that you set the user-domain to mtu.edu. Otherwise, Pine will include the machine name of the computer you r working on in the e-mail address. As an example, if you are working on civlab9.civil and you enter your user ID on the From line with no domain name (i.e. mtu.edu), Pine will think you e-mail address is userid@civlab9.civil.mtu.edu. If someone tries t o reply to this address, it will not work and the message will bounce back to the sender as undeliverable.