Physical Cryptography
Abstract: Physical cryptosystems base their security underlying inherently complex physical systems. They can potentially provide high levels of complementary security to existing standard cryptosystems, which are in principle vulnerable against new hardware or algorithms due to their unproven mathematical assumptions and loopholes. Physical cryptography can also have advantages over quantum cryptography (special kind of physical cryptography that exploits quantum states), which demands highly sophisticated techniques to distribute the fragile quantum states. However, although many physical cryptosystems have been proposed, the search for quantifiable security and simultaneously practical implementation still continues. In this project we study how to evaluate the performance and security of these new cryptography schemes. In particular, we search for reliable and quantifiable security analysis techniques to assess those systems.
Keywords: Cryptography
Collaborators: Sadik Esener (UC San Diego)
Secure cryptosystems is among the most important topics of information science and technologies [1]. Physical cryptosystems base their security underlying inherently complex physical systems (Figure 1). They can potentially provide high levels of complementary security to existing standard cryptosystems, which are in principle vulnerable against new hardware such as quantum computers or algorithms due to their unproven mathematical assumptions and loopholes. Illegitimate parties can compromise the binary keys generated by standard techniques, because these keys are based on existing concepts and can be extracted from mobile environments or computers by malicious software, viruses, or Trojan horses and hence lead to important security breaches.

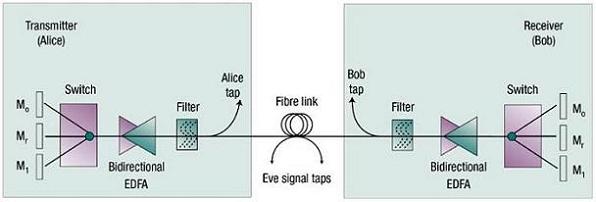
Figure 1 A typical physical cryptography system. Alice and Bob can create a cryptographic key by randomly switching between mirrors representing '0' or '1' (Mo or M1; Mr is a reset mirror) [2]
In this project we analyze an alternative approach to standard cryptography called physical cryptography [3-6] which is based on inherently complex photonic systems. It does not rely on various mathematical techniques used at present or quantum physics. Physical cryptosystems can have strong security advantages over conventional systems. It offers useful complementary approaches for protecting sensitive communications. Some of the important applications beside encryption can be listed as secure key generation and exchange, hardware protection against tampering, secure authentication over insecure networks, digital rights management and IP protection, and secure sensors.
How is the physical cryptography different from quantum cryptography? Quantum cryptography is only a special type of physical cryptography, which is based on distributing shared secret keys for cryptographic purposes by employing the laws of quantum physics. It has been studied extensively over 20 years. Although quantum key distribution systems provide very high level of security, fragile quantum states render the technical demands such as efficient single-photon emission and detection for high-performance practical cryptosystems highly difficult to be met in near future.
In contrast, physical cryptography which does not rely on quantum physics can potentially offer practical security in a significantly more robust and less expensive way than quantum cryptography [2]. However, although many physical cryptosystems have been proposed, the search for quantifiable security and simultaneously practical implementation still continues. These interesting and potentially important new systems require substantial and detailed security analysis. In this project we study how to evaluate the performance and security of these new cryptography schemes. In particular, we search for reliable and quantifiable security analysis techniques to assess such all-optical physical cryptosystems.
References
[1] Physical Cryptography Project, Technische Universitat Munchen, http://www.dnd-solo.de
[2] G. S. Kanter and P. Kumar, Fibre Lasers: Keeping cryptographic keys safe, Nature Photonics 1, 15 (2006).
[3] J. Scheuer and A. Yariv, Giant Fiber Lasers: A New Paradigm for Secure Key Distribution, Phys. Rev. Lett. 97, 140502 (2006).
[4] H. Hodara, Secure Fiberoptic Communications, Fiber Integ. Opt. 22, 47 (2003).
[5] L. B. Kish, Totally secure classical communication utilizing Johnson (-like) noise and Kirchoff's law, Phys. Lett. A 352, 178 (2005).
[6] H. P. Yuen and A. M. Kim, Classical noise-based cryptography similar to two-state quantum cryptography, Phys. Lett. A 241, 135 (1998).